서버 배포 / DevOps 구성
CI/CD 구성
Github를 활용한 tag로 분리하여 배포진행함 Github Action Tag -> Build Dockerimage to Azure ACR with Helm Image -> ArgoCD Deploy for Kubernetes -> Auto update service
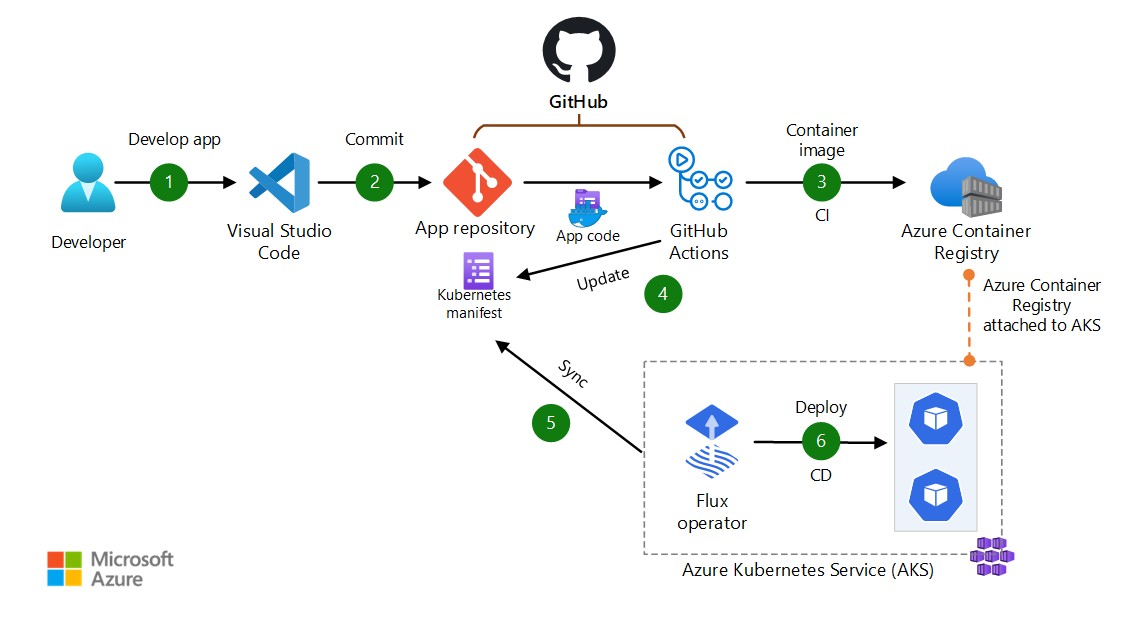
ArgoCD 설치 for CI/CD API server
ArgoCD 링크 (opens in a new tab) - Azure Login기능 적용 Terraform을 활용하여 인프라 코드로 Helm를 활용한 Kubernetes에 배포하여 관리하고 있습니다. 아래와 같이 helm을 통해서 argocd를 설치하며 기타 OIDC, RBAC, DNS, Ingress를 설정하여 외부에서 접근 가능하도록 설정되어있습니다.
resource "helm_release" "argocd" {
name = var.namespace
repository = "https://argoproj.github.io/argo-helm"
chart = "argo-cd"
version = "5.46.7" # 원하는 버전 지정
namespace = var.namespace
set {
name = "server.service.type"
value = "ClusterIP"
}
set {
# Run server without TLS
name = "configs.params.server\\.insecure"
value = true
}
depends_on = [
kubernetes_namespace.argocd,
null_resource.add_helm_repo
]
}
resource "azuread_service_principal" "sp" {
depends_on = [azuread_application.app]
application_id = azuread_application.app.application_id
app_role_assignment_required = false
}
resource "azuread_application_password" "password" {
display_name = "argocd-sso"
depends_on = [azuread_application.app]
application_object_id = azuread_application.app.object_id
end_date_relative = "8640h" # 예: 1년 후 만료
}
resource "kubectl_manifest" "argocd_cm" {
yaml_body = <<-EOT
apiVersion: v1
kind: ConfigMap
metadata:
name: ${var.namespace}-cm
namespace: ${var.namespace}
labels:
app.kubernetes.io/component: server
app.kubernetes.io/instance: ${var.namespace}
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: ${var.namespace}-cm
app.kubernetes.io/part-of: ${var.namespace}
app.kubernetes.io/version: v2.8.3
helm.sh/chart: argo-cd-5.46.2
annotations:
meta.helm.sh/release-name: ${var.namespace}
meta.helm.sh/release-namespace: ${var.namespace}
data:
admin.enabled: "${var.argocd_admin_enabled}"
application.instanceLabelKey: ${var.namespace}.argoproj.io/instance
exec.enabled: "false"
server.rbac.log.enforce.enable: "false"
timeout.hard.reconciliation: "0s"
timeout.reconciliation: "180s"
url: "https://${local.dns_link}"
dex.config: |
connectors:
- type: microsoft
id: microsoft
name: Azure AD
config:
clientID: "${azuread_application.app.application_id}"
clientSecret: "${azuread_application_password.password.value}"
redirectURI: "https://${local.dns_link}/api/dex/callback"
tenant: "${data.azurerm_client_config.current.tenant_id}"
EOT
depends_on = [azuread_application.app, azuread_application_password.password]
}
resource "kubectl_manifest" "argocd_rbac-cm" {
yaml_body = <<-EOT
apiVersion: v1
kind: ConfigMap
metadata:
name: ${var.namespace}-rbac-cm
namespace: ${var.namespace}
labels:
app.kubernetes.io/component: server
app.kubernetes.io/instance: ${var.namespace}
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: ${var.namespace}-rbac-cm
app.kubernetes.io/part-of: ${var.namespace}
app.kubernetes.io/version: v2.8.3
helm.sh/chart: argo-cd-5.46.2
annotations:
meta.helm.sh/release-name: ${var.namespace}
meta.helm.sh/release-namespace: ${var.namespace}
data:
policy.csv: |
p, role:org-admin, applications, *, */*, allow
p, role:org-admin, clusters, get, *, allow
p, role:org-admin, repositories, get, *, allow
p, role:org-admin, repositories, create, *, allow
p, role:org-admin, repositories, update, *, allow
p, role:org-admin, repositories, delete, *, allow
g, "${data.azuread_group.admin.display_name}", role:org-admin
policy.default: role:readonly
scopes: "[openid, profile, email, groups]"
EOT
depends_on = [azuread_application.app, azuread_application_password.password]
}